Just when you think your cyber security setup is solid — BAM — a new threat surfaces that changes the game.
This time, it’s not about guessing passwords or cracking weak logins. It’s not even about tricking someone into clicking a suspicious link.
Instead, hackers are now exploiting the very systems designed to keep you safe — and they don’t even need your password to do it.
Microsoft has issued a fresh warning about a rising tactic that’s targeting businesses of all sizes. It’s subtle, highly convincing, and dangerous because it uses legitimate Microsoft infrastructure to bypass traditional security measures.
Yes, even multi-factor authentication.
It’s a whole new kind of phishing — and chances are, your team wouldn’t even realise it’s happening.
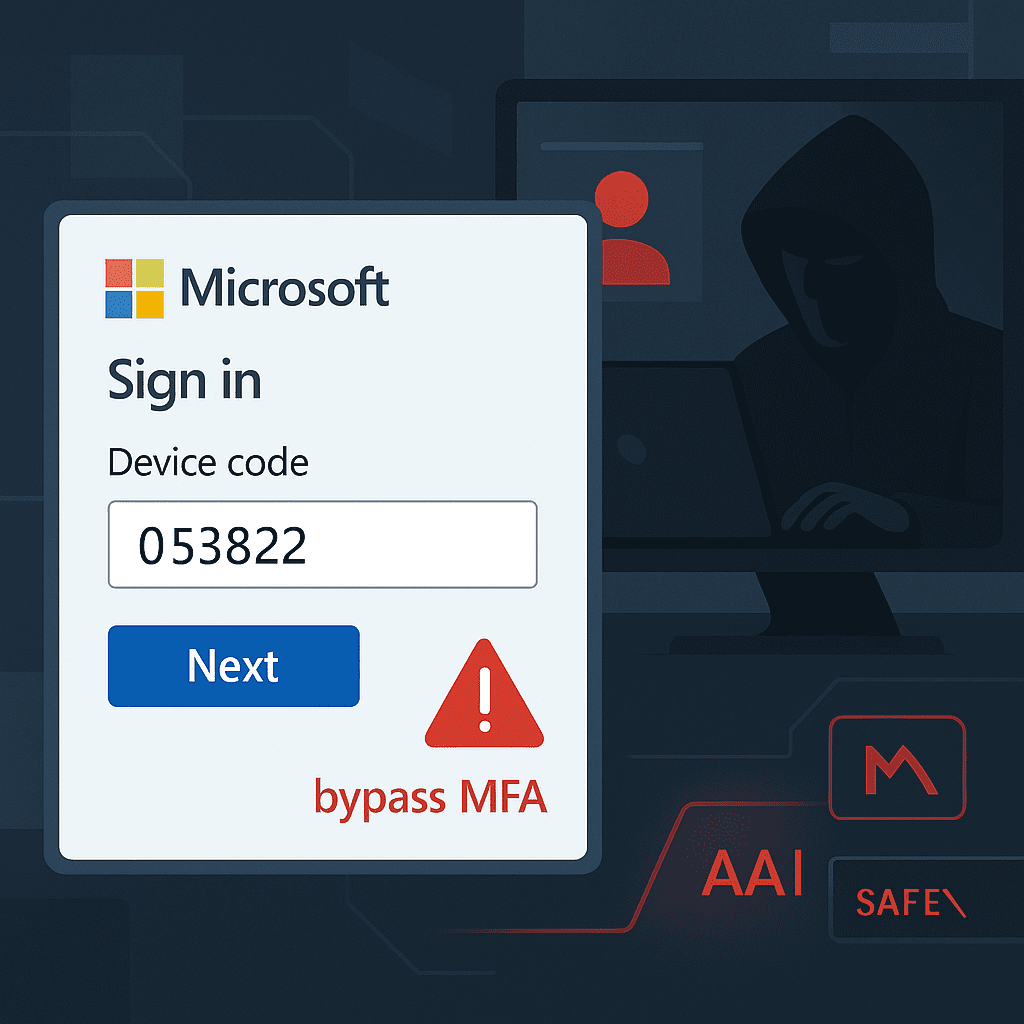
Microsoft has flagged a growing wave of attacks using a tactic called device code phishing. It’s clever, subtle, and far more convincing than your typical phishing attempt.
Most phishing scams trick you into typing your password into a fake website. This one? It tricks you into giving away access voluntarily — and it does it using real Microsoft login pages.
It usually starts with a believable email. It might appear to come from HR or a colleague, inviting you to a Microsoft Teams meeting.
You click the link and land on an official-looking Microsoft login page. So far, everything feels normal.
Then comes the twist.
You’re prompted to enter a short device code (which was included in the email). You’re told it’s required to join the meeting or finish logging in.
But here’s what’s actually happening:
You’re not logging yourself in. You’re logging them in.
That device code is linked to the attacker’s device — so by entering it, you’re authorising access to your account on their machine.
Worse still? Because it’s all happening through legitimate Microsoft systems, it can even bypass multi-factor authentication (MFA). Yes, even if you have extra security in place.
The login screen is real
The code seems legit
There’s no obvious red flag
That’s why it works. It feels completely normal — until it’s too late.
Once inside, attackers can:
Read your emails
Access and download files
Send messages pretending to be you
Spread scams internally through your account
And because they’re often granted a session token (a digital pass that keeps you logged in), they can stay in your account even after you change your password.
1. Train your team to be cautious with login requests
If someone sends a device code, pause. Ask yourself:
Did I request this? Do I know it’s legitimate?
If not, verify it using a separate method like a direct phone call or internal chat.
2. Remember this rule
Microsoft logins don’t involve someone else giving you a code. If you’re asked to enter a code someone else provided, that’s a red flag.
3. Limit device code login
Ask your IT team (or provider) to disable device code authentication if your business doesn’t need it.
4. Enforce location or device-based login rules
This helps limit access to trusted networks and known devices only.
5. Keep cyber awareness training ongoing
The more your team knows, the safer your business is. Prevention starts with awareness.
We can help you identify risks, disable unnecessary login methods, and roll out smarter protections across your business. Let’s make sure your team stays ahead of these evolving threats.
Get in touch today.